As cyber security becomes the domain of organised crime every Australian individual and business has become an unwilling, unwelcome target. Data breaches are hitting big business too, from Bupa to Nvidia and Optus. Law firms, perhaps slower to embrace technology, now face the ever more complex threat of cyber security compromise and it’s easy to feel the urge to regress off grid… ditch the paperless office in favour of old-school pen and paper files.
Before you embrace your inner doomsday prepper, we caught up with Lawcover’s Legal Risk Manager, Glenda Carry, to find out how law firms are being targeted by cyber security threats, what these attacks look like, and what steps they can take to mitigate risk.
Business email compromise impacting settlements and major transactions
“Cyber security is a significant concern for all law practices as solicitors hold not only sensitive data but also carry out transactions involving large sums of money,” Glenda says.
Major data breaches affecting some of Australia’s high-profile organisations have dominated headlines. And according to Glenda, at a law firm level the picture is a little different.
“From what we are seeing in terms of notifications from smaller practices, the main concern is Business Email Compromise [BEC].”
This predominantly affects conveyancing firms.
“We do see some notifications relating to ransomware and data breaches but not as many as that relate to BEC. BEC involves fraudulent emails sent by cybercriminals impersonating a real business, organisation, employee, client or contact,” Glenda explains.
“The emails often involve a change in bank account details. What this typically looks like is that the cybercriminal accesses the email system of a client or law practice. Once in, the cybercriminal changes the email ‘rules’ so that legitimate emails from a particular sender (e.g. a client containing bank account details) are automatically sent to an archive/trash folder. The cybercriminal then communicates with the client or law practice and provides fraudulent bank account details.”
While BEC involves criminals accessing confidential client information, the main objective is generally not stealing client data - but simply facilitating the fraudulent transfer of funds.
“Cybercriminals often sit quietly in the client or law practice’s email system for some time observing email exchanges between the solicitor and client, so as to replicate the emails without arousing suspicion,” Glenda says. “The cybercriminals often choose to act shortly before a deadline such as a conveyancing settlement. Settlements taking place on a Friday before a public holiday tend to be particularly at risk.”
It is a nefarious approach that plays into human error, trust and timing. It is also an approach that works. Set out below is a table that illustrates the claims losses and expenses incurred by Lawcover in respect of cyber assisted fraud claims.
“As you can see from the statistics, BEC can involve high-value claims,” Glenda shares. “While they predominantly affect conveyancing firms, BEC can affect all firms where monies are being transferred, such as in the distribution of estates, settlement of litigation etc.” 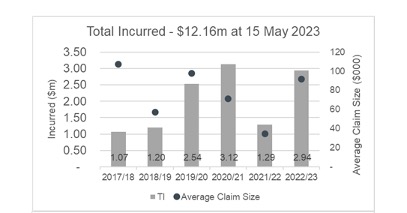
Sensitive information most at risk, compromised by insecure technology
Despite the prevalence of BEC, data breaches are also a concern for law firms. At present, law practices with an annual turnover less than $3M may not be subject to the Australian Privacy Principles set out in the Privacy Act 1988 (Cth). However, this is currently under review Glenda cautions.
“Regardless of turnover, solicitors need to be mindful of their duty to maintain client confidentiality. Law practices have an obligation to protect confidential and sensitive information and to respond quickly and appropriately where there is a risk that this information has been or may be disclosed.”
Law firms thrive on trust. Indeed, their fiduciary duties to maintain client confidentiality reflect this. However, as law firms store vast amounts of sensitive information via electronic repositories, few are aware of how effectively secure their systems may be.
“Data is an increasingly valuable resource, and therefore attractive to cybercriminals,” Glenda warns.
While there are many aspects of a law practice that are vulnerable to cyber-attack, there are a number of key areas that are consistently targeted. These include:
- Physical IT: computers, servers, storage devices, network and mobile devices;
- Human Error: choosing insufficiently complex passwords, clicking on compromised links, accessing insecure wifi, or any other issues designed to play into human error;
- Personal Equipment: Personal phones and devices which may not be as secure as corporate IT equipment.
8 Steps law practices can take to mitigate cyber risk
Worrying about cyber security can feel like an unwelcome addition to a to-do list, but Glenda says there is no need to be overwhelmed.
“The good news is that there are many simple and easy-to-implement steps that can be incorporated into everyday practice to minimise the risk of becoming a victim of cyber fraud.”
Here are 8 cyber security steps that Glenda advises for law firms:
- Complete Lawcover’s Cyber Risk Assessment Tool, which helps you assess your firm’s cyber risk awareness and preparedness. Available online; the results remain anonymous. Review the Cyber Risk Management Checklist, a collaborative effort of Lawcover and the Law Society of NSW. This can help you prepare a cyber response plan for what to do in the event of a cyber-attack.
- Never assume that emailed bank account details are correct. Always verify bank account details with the sender by telephone or other non-email means. Once verified, file note the conversation. Ensure all staff are trained to follow the verification process. Always treat last minute emails advising of a change of bank account details with suspicion.
- Educate your clients on the risk of cyber fraud, especially with emailed bank account details. Tell your clients that you will not change account details via email, and ask them to call and confirm bank account details prior to transferring funds.
- Regularly check your email set up to ensure that there are no unexpected redirection rules in place. In Microsoft Outlook, you can check this on the Home screen > Rules > Manage Rules > Alerts.
- Do not click on links or attachments in suspicious emails.
- Install antivirus protection software and keep it up to date. Install new software patches when available.
- Back-up data daily and check regularly to ensure back-ups are working properly.
- Ensure passwords are unique and changed regularly.
Developing a Cyber Security Response Plan
Hope for the best but prepare for the worst. As the worst takes on a new cyber security dimension, developing a Cyber Security Response Plan is becoming an increasingly common feature of well-prepared firms.
According to Glenda, a good Cyber Security Response Plan might include:
- Theft of funds process: Where the cyber-attack involves transfer of funds, you may have a process in place to manage the immediate next steps. This may include having contact details for your bank’s fraud team handy and calling the bank immediately to advise of the suspected fraudulent transaction. If the cybercrime relates to trust money, report the incident to the Law Society’s Trust Accounts Department.
- Cyber Insurance: Lawcover provides cyber risk insurance, which is specific to the risks faced by law practices. Firms insured with Lawcover have access to this policy at no additional cost. It includes crisis management costs, electronic business interruption and cyber liability to third parties. If you suspect your cyber security has been compromised, you can call Lawcover’s Cyber Response Team to access your cyber risk insurance cover on 1800 BREACH. The policy limit for each law practice is $50,000 for all cover under the policy, during the period of insurance. As this may or may not be sufficient, firms are advised to consider whether additional cover ought to be purchased.
- We strongly urge law practices to have Lawcover’s Cyber Response Team’s number to hand – 1800 BREACH (1800 273 224).
- Notify your IT provider and, if relevant, your legal practice management software provider.
- Contact Lawcover’s claim solicitors who can guide you through next steps.
- Comply with your obligations to notify an ‘eligible data breach’ under the Privacy Act 1988 (Cth). Report the incident to the police (where appropriate) and the Australian Cyber Security Centre.
“Dealing with a cyber-attack can be very stressful which is why contingency planning is key,” Glenda advises. Cyber security training may also be worth considering.
“Every law practice is different, each practice should consider its own circumstances when seeking appropriate cyber security training,” Glenda says. “Lawcover has recently published a suite of online cyber resources specifically created for law practices with practical and detailed ‘how-to guides’ to strengthen cyber defences.”









































![How to handle Direct Speech after Gan v Xie [2023] NSWCA 163](https://images4.cmp.optimizely.com/assets/Lawyer+Up+direct+speech+in+drafting+NSW+legislation+OCT232.jpg/Zz1hNDU4YzQyMjQzNzkxMWVmYjFlNGY2ODk3ZWMxNzE0Mw==)













































